C# - FreeBSD にインストール - インストール - ports
- 1. インストール
- 2. インストール時のメッセージ
1. インストール
参考サイトの通りにやってみます。
「mono」という「ports」をインストールするらしい。
「ウィキペディア - Mono」を読んでやっと合点がいきました。
cd /usr/ports/lang/mono
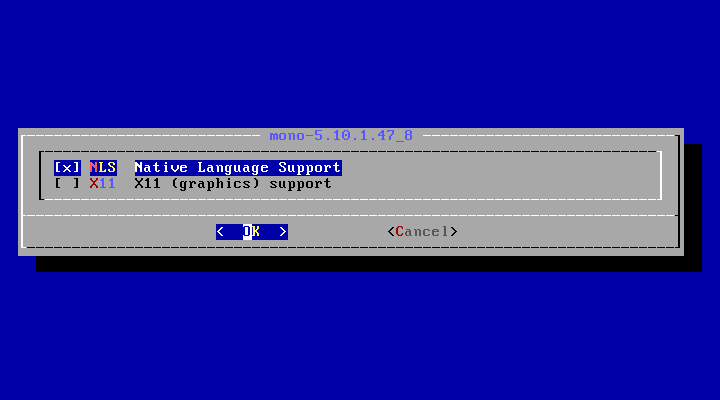
make config
グラフィックス関係なければ、「X11」は、はずします。
cd /usr/ports/lang/mono
make
「make」の途中でこける・・・。
おしりのほうだけね。
=> SHA256 Checksum OK for xorg/xserver/xorg-server-1.19.1.tar.bz2.
===> Patching for xorg-vfbserver-1.19.1_9,1
===> Applying extra patch /usr/ports/x11-servers/xorg-vfbserver/../xorg-server/files/patch-CVE-2017-12176
===> Applying extra patch /usr/ports/x11-servers/xorg-vfbserver/../xorg-server/files/patch-CVE-2017-12177
===> Applying extra patch /usr/ports/x11-servers/xorg-vfbserver/../xorg-server/files/patch-CVE-2017-12178
===> Applying extra patch /usr/ports/x11-servers/xorg-vfbserver/../xorg-server/files/patch-CVE-2017-12179
===> Applying extra patch /usr/ports/x11-servers/xorg-vfbserver/../xorg-server/files/patch-CVE-2017-12183
===> Applying extra patch /usr/ports/x11-servers/xorg-vfbserver/../xorg-server/files/patch-CVE-2017-1218x
===> Applying extra patch /usr/ports/x11-servers/xorg-vfbserver/../xorg-server/files/patch-CVE-2017-1218y
===> Applying extra patch /usr/ports/x11-servers/xorg-vfbserver/../xorg-server/files/patch-CVE-2017-13721
===> Applying extra patch /usr/ports/x11-servers/xorg-vfbserver/../xorg-server/files/patch-CVE-2017-13723
===> Applying extra patch /usr/ports/x11-servers/xorg-vfbserver/../xorg-server/files/patch-os_io.c
===> xorg-vfbserver-1.19.1_9,1 depends on package: libepoxy>0 - not found
===> libepoxy-1.4.3 needs Python 3.3 at least, but 2.7 was specified.
*** Error code 1
Stop.
make[4]: stopped in /usr/ports/graphics/libepoxy
*** Error code 1
Stop.
make[3]: stopped in /usr/ports/x11-servers/xorg-vfbserver
*** Error code 1
Stop.
make[2]: stopped in /usr/ports/x11-servers/xorg-vfbserver
*** Error code 1
Stop.
make[1]: stopped in /usr/ports/lang/mono
*** Error code 1
Stop.
make: stopped in /usr/ports/lang/mono
えっ?
「python2.7」と「python3.6」はあるんだが・・・。
「/usr/ports/graphics/libepoxy」ってやつは「python3.3」をピンポイントで必要とするらしい・・・
当初、「X11」のオプションをつけておりまして、「/usr/ports/graphics/libepoxy」ってくらいだから「X11」のオプションをはずして、左記へ進めました。
オプションをはずしてしきりなおし。
cd /usr/ports/lang/mono
make clean
make
make install
しかし、「make」の時点で恐ろしく時間がかかります。数時間?
2. インストール時のメッセージ
インストール時のメッセージは、後で影響するかもしれないので記録しておきます。
===> Installing for mono-5.10.1.47_8
===> Checking if mono already installed
===> Registering installation for mono-5.10.1.47_8
Installing mono-5.10.1.47_8...
************************************************************************
If you have build/runtime errors with Mono and Gtk# apps please try the
following first:
* Build Mono and gtk+ (x11-toolkits/gtk20) without CPUTYPE and with the
default FreeBSD CFLAGS ('-O2 -fno-strict-aliasing -pipe') as Mono has
been known to expose compiler bugs.
* Try building and running Mono with the GENERIC kernel.
- Mono requires SYSVSHM, SYSVMSG, and SYSVSEM which are part of the
GENERIC kernel.
- Removing kernel options or changing defaults to use experimental
options can adversely affect Mono's ability to build and run.
* Remove leftover semaphores / increase semaphore limits.
- Close apps which use Mono and run `ipcs -sbt`. Remove the
semaphores with MODE "--rw-------" and NSEMS "8" using ipcrm (1)
- _OR_ simply reboot which is the safest method.
- On multi-user systems the semaphore limits may need to be increased
from the defaults. The following should comfortably support 30 users.
# echo "kern.ipc.semmni=40" >> /boot/loader.conf
# echo "kern.ipc.semmns=300" >> /boot/loader.conf
* If you are in a jailed environment, ensure System V IPC are enabled.
You can rely on the security.jail.sysvipc_allowed sysctl to check
this status. The following enables this feature on the host system:
# echo "jail_sysvipc_allow=\"YES\"" >> /etc/rc.conf
* Some process information are accessed through /proc (e.g. when using
NUnit) and procfs(5) has to be mounted for these features to work:
# echo "proc /proc procfs rw 0 0" >> /etc/fstab
************************************************************************
===> SECURITY REPORT:
This port has installed the following files which may act as network
servers and may therefore pose a remote security risk to the system.
/usr/local/lib/libmono-profiler-log.so.0.0.0
/usr/local/lib/libmonoboehm-2.0.a(libmonoruntime_la-w32socket-unix.o)
/usr/local/lib/libmonoboehm-2.0.so.1.0.0
/usr/local/lib/libmonosgen-2.0.a(libmonoruntimesgen_la-w32socket-unix.o)
/usr/local/lib/libmonoboehm-2.0.a(libmini_la-debugger-agent.o)
/usr/local/bin/mono-sgen
/usr/local/lib/libmonosgen-2.0.a(libmonoruntimesgen_la-attach.o)
/usr/local/lib/libmonosgen-2.0.so.1.0.0
/usr/local/lib/libmonosgen-2.0.a(libmini_la-debugger-agent.o)
/usr/local/lib/libmonoboehm-2.0.a(libmonoruntime_la-attach.o)
/usr/local/bin/pedump
/usr/local/lib/libmono-profiler-log-static.a(log.o)
/usr/local/lib/libMonoPosixHelper.a(sys-socket.o)
/usr/local/lib/libmono-profiler-log.a(log.o)
/usr/local/lib/libMonoPosixHelper.so
/usr/local/bin/monodis
/usr/local/bin/mono-boehm
If there are vulnerabilities in these programs there may be a security
risk to the system. FreeBSD makes no guarantee about the security of
ports included in the Ports Collection. Please type 'make deinstall'
to deinstall the port if this is a concern.
For more information, and contact details about the security
status of this software, see the following webpage:
http://www.mono-project.com/
|
|